On September 11, 2023, MGM Resorts publicly disclosed a “cybersecurity incident” affecting their systems. It was revealed that a hacker group known as “Scatter Spider” had employed ransomware-as-a-service created by BlackCat, also known as ALPHV. These hackers used Open Source Intelligence (OSINT) collected from LinkedIn and other sources to gather just enough information about a high-value user. They then executed a vishing attack on the resort’s help desk in an attempt to obtain credentials and access and infect the systems [1]. Scatter Spider’s reconnaissance equipped them with sufficient information about the company, its systems, and the targeted individual.
This situation raises the question of who bears the true responsibility. Is it the employee who had just enough publicly available information to be impersonated? Is it the employee assisting in the account reset? Or is it the stakeholders for failing to implement better identity verification practices? Based solely on publicly released information, it appears that the shareholders share some of the blame. MGM Resorts is a multi-billion-dollar company, and it should not be easy to impersonate an employee and gain access to their network. Multiple layers of authentication should be in place to verify the identity of high-value employees. Moreover, high-value employees should undergo a separate and rigorous identity confirmation process, especially in situations like these. Should there be a separation of duties for high-value employees? If so, perhaps someone could have identified vulnerabilities in their story, preventing a successful vishing attack. Can trust changes be monitored? But let’s not digress; let’s continue with the story.
MGM detected Scatter Spider within their Okta Sync Server, where the hackers were sniffing passwords. Presumably, they were attempting to crack passwords that they couldn’t decipher from the domain hush dump [2]. The hackers gained persistence when they accessed the Okta tenant through the “inbound federation” feature, most likely due to password reuse by employees. With an established foothold, the attackers proceeded to move laterally through MGM’s network, gaining access to their Microsoft Azure cloud environment. MGM employs Azure Cloud Services for application hosting and computing services [3]. By this point, Scatter Spider had successfully exfiltrated terabytes of data.
In response to the presence of hackers within the network, MGM terminated the Okta platform, resulting in further outages of MGM’s services. However, the outages did not end there. Hackers leveraged their escalated privileges to deploy Ransomware-as-a-Service, developed by BlackCat. They used this ransomware to encrypt ESXi servers that hosted virtual machines for MGM [2]. During the cyber-attack, MGM hotels were unable to issue digital key cards, facilitate check-in/out procedures, operate gambling machines, process card payments, and more [2]. This led to visitors enduring long lines with wait times stretching into hours.
MGM Resorts experienced a daily revenue reduction of 10%-20%, resulting in losses of approximately 8.4 million dollars each day that their systems remained down. Notably, MGM made no attempt to pay the undisclosed ransom. Instead, it appears that they are aggressively hiring to monitor and rebuild their environment from the ground up.
Undergoing a cyberattack places organizations under tremendous stress, especially when the company generates millions of dollars in daily revenue. Numerous questions come to mind as I read about this event. Has this attack harmed MGM Resorts’ credibility and reputation? Why would visitors continue to frequent MGM if they fear their data will not be adequately protected and may potentially be leaked? Did the resort have an effective incident response plan in place? Based on the reports, it seems that MGM may have made some hasty decisions, which suggests that a proper plan may not have been enacted. I would be interested in hearing the lessons learned from these events.
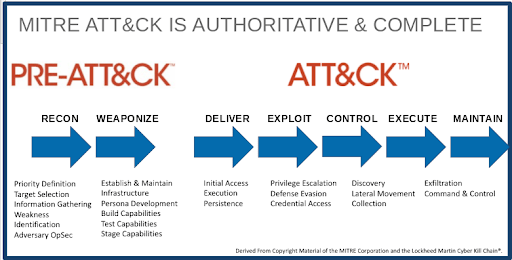
This cyber attacker demonstrated a proficient use of the MITRE ATT&CK framework, particularly in the phases of delivery, exploitation, control, execution, and maintenance:
- Delivery: They successfully executed a vishing attack to gain access to the high-value user’s account.
- Exploit: Stolen credentials were used to complete privilege escalations and gain access to additional systems, particularly Okta Servers.
- Control: Lateral movement within MGM’s networks allowed them to gain and maintain access to other systems, including ESXi servers.
- Execute: They exfiltrated and encrypted MGM’s data.
- Maintain: Scatter Spider established a foothold within the environment.
References
[1] S. Morrison, “The chaotic and cinematic MGM casino hack, explained,” Vox, 21 September 2023. [Online]. Available: https://www.vox.com/technology/2023/9/15/23875113/mgm-hack-casino-vishing-cybersecurity-ransomware. [Accessed 30 September 2023].
[2] A. Thompson, “The MGM Resorts Attack: Initial Analysis,” CyberARK, 22 September 2023. [Online]. Available: https://www.cyberark.com/resources/blog/the-mgm-resorts-attack-initial-analysis. [Accessed 31 September 2023].
[3] Apps Run The World, “MGM Resorts International selects Microsoft Azure Cloud Services for Application Hosting and Computing Services,” Apps Run The World, [Online]. Available: https://www.appsruntheworld.com/customers-database/purchases/view/mgm-resorts-international-united-states-selects-microsoft-azure-cloud-services-for-application-hosting-and-computing-services. [Accessed 4 October 2023].
SlideShow Citation:
Image Number 2: Andy Thompson / CyberArc Article
Image Number 3: K.M. Cannon / Las Vegas Review-Journal / Tribune News Service / Getty Images
“Everyone has a plan until they get punched in the mouth.”
— Mike Tyson
Breaking Into Cyber Security
Proudly Powered by WordPress